DDoS – Did You Know? Stay Ahead of Attackers
Story by Ellyce Hill, Strategic Communications Intern, Summer 2023
Did you know that in today’s interconnected world, cyber-attacks can happen at any moment? Cyberthreats have continued to evolve and change alongside the internet and technology. These threats have only matured over time, so it is important to stay educated on the latest attacks to take the necessary steps to prevent them. In this article, we’ll explore DDoS or Distributed Denial-of-Service Attacks, uncover the motives and techniques behind these attacks and how to protect your organization from becoming a victim.
Let’s dive into the world of DDoS attacks and learn how to empower ourselves to stay one step ahead in the game of cybersecurity.
What are DDoS Attacks?
DDoS Attacks or Distributed Denial-of-Service attacks are a type of cyberattack that floods a company’s network infrastructure with traffic. According to Radware’s 2023 report organizations around the world mitigate an average of 29.3 attacks per day.
If websites begin to buffer, error messages start to load, and your internet circuit is maxed out, this could be a sign that your organization may be the victim of an attack. Attacks come from individuals finding weaknesses in the software or depleting bandwidth. DDoS attacks can delay communication and prevent employees from accessing important information. Understanding the basics of DDoS Attacks can help prevent them in the future.
Click here to learn more about DDoS Attacks.
Botnets
Botnets are often used in DDoS attacks. They are created by infecting computers with malware. This allows attackers to control devices through computers on the infected network remotely.
The Three Types of Attacks
Volumetric
This is the most common type of attack. A targeted organization will receive unwanted traffic with devices compromised by botnets. These attacks will exploit the weaknesses of a network’s infrastructure. It seeks to overwhelm the network’s capacity and can block staff from accessing their information.
Application-Layer
Application or Layer 7 attacks can negatively impact an application’s ability to communicate with other applications on different computer systems and networks. Its goal is to disrupt applications or services by exploiting weaknesses in the application layer. This could hinder communication by preventing users from sending or receiving messages.
Protocol
Also known as network layer attacks, they can negatively impact the TCP/IP, DNS, and ICMP protocols in an organization’s network. The protocols are responsible for communication between devices and their network resulting in network downtime, data theft, or system compromise.
Network Infrastructure is a Key Part of Defense
Securing network infrastructure requires a multi-layered approach to protecting subscriber data. This can include regular testing, network segmentation, load balancers, and content delivery markets.
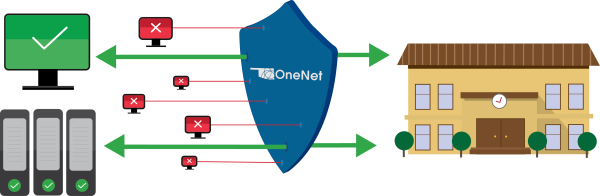
OneNet Provides DDoS mitigation
OneNet’s solution provides DDoS mitigation without compromising organizations’ time and at no additional cost to subscribers. Real-time traffic alerts and comprehensive analysis tools provide visibility into network activity, ensuring a proactive response.
DDoS Mitigation in K-12 Schools
State testing season can be stressful for teachers, students, and their school’s virtual network. These periods are known for their high traffic and activity, so regular mitigation becomes necessary. OneNet’s strategies and protective security controls help schools detect DDoS Attacks before they happen. Without OneNet, many schools would not be able to complete their state testing.
Questions about DDoS mitigation? Email us at info@onenet.net.